Does it feel like your computer slows down after spending an extended time watching YouTube? Well, that could have something to do with YouTube serving ads that allow cryptocurrency miners to use your system resources to mine for them.
[Rant] Tech Whine Like a baby thread
- Thread starter DarkAudit
- Start date
More options
Export threadGasBandit
Staff member
Yet another example of how ad blockers are just required self defense, these days.Does it feel like your computer slows down after spending an extended time watching YouTube? Well, that could have something to do with YouTube serving ads that allow cryptocurrency miners to use your system resources to mine for them.
And sites that block me for using ad blockers make me want to spend extra at their competition out of spite.Yet another example of how ad blockers are just required self defense, these days.
GasBandit
Staff member
Try AdNauseam. It fools the websites into thinking you're loading and clicking the ads. It even works on Forbes, which as Pez says below, is one of the worst offenders.And sites that block me for using ad blockers make me want to spend extra at their competition out of spite.
Last edited:
figmentPez
Staff member
You mean like Forbes... which serves up malware in its ads? I can't find the article I read recently on it, but basically it said that sites that try to prevent you from viewing them without ad blockers are the most likely to have ads that contain malware.And sites that block me for using ad blockers make me want to spend extra at their competition out of spite.
Does it run the javascript from the ad? If so, it still puts you at risk for malware and coin mining ads.Try AdNauseam. It fools the websites into thinking you're loading and clicking the ads.
GasBandit
Staff member
I'm not 100% on this, because the dev faq is a skosh deep for my casual blood, but the way I understand it, the sandbox only keeps static image ads in its "collection," and discards video/animated/dynamically generated ads. It doesn't actually load or run embedded code in ads, it just downloads the data, and then depends on the html tag/iframe for instructions on how to report the ad "clicked." If the info is in the ad's JS, then it doesn't, because it discards any ad that is not a static image as soon as it is downloaded (and it only keeps the images so it can build you a smug mosaic cloud of all the ads you didn't have to see, thanks to it). At least that is my understanding.Does it run the javascript from the ad? If so, it still puts you at risk for malware and coin mining ads.
And now the stripping out of unnecessary junk begins. And the turning off of Windows' oh-so-helpful attempts to be helpful. Like the stupid game overlay that constantly popped up whenever I launched a game and told me to "hit <camera icon> to take a screenshot" or "press <rewind button> to see what you just did!" Ok, first, I just did whatever it was I just did. Why would I need to immediately rewind and see what I did? Secondly, you wanna know what I did? I logged in! Oooo... pretty video of someone logging in!
Also, Windows absolutely refused to allow me to use a password to secure my computer. I had no choice but to set a PIN. It really wanted me to use a unique four-digit numerical PIN, but I turned on alphanumeric mode and made my PIN 'fuckyou'. So, if anyone is ever at my place, and they need to get into my computer, the super-secret, ultra-secure seven letter PIN that totally won't be as guessable as an 11 character alphanumeric string with special characters thrown in, is fuckyou.
Also, Windows absolutely refused to allow me to use a password to secure my computer. I had no choice but to set a PIN. It really wanted me to use a unique four-digit numerical PIN, but I turned on alphanumeric mode and made my PIN 'fuckyou'. So, if anyone is ever at my place, and they need to get into my computer, the super-secret, ultra-secure seven letter PIN that totally won't be as guessable as an 11 character alphanumeric string with special characters thrown in, is fuckyou.
It's there. They hide it, but it's there. You CAN set up Windows without having to create an online Microsoft account, just like you can set up a Macintosh without having to create an Apple ID, but both of them make it non-obvious how to do so, because they would prefer that you did.Windows absolutely refused to allow me to use a password to secure my computer.
--Patrick
If there was a way to prevent it from requiring a PIN at install, they hid it deep. Even when I chose "not now," or "cancel" the only thing it would do is go back to that same screen again - a keypad with no numbers on it and "Would you like to set a PIN now?"It's there. They hide it, but it's there. You CAN set up Windows without having to create an online Microsoft account, just like you can set up a Macintosh without having to create an Apple ID, but both of them make it non-obvious how to do so, because they would prefer that you did.
--Patrick
Of course, it also refused to allow me to use the keyboard or mouse to select options during setup - preferring instead that I apparently shout at Cortana with no microphone, because it absolutely refused to believe that this is a desktop computer and not a phone or tablet.If there was a way to prevent it from requiring a PIN at install, they hid it deep. Even when I chose "not now," or "cancel" the only thing it would do is go back to that same screen again - a keypad with no numbers on it and "Would you like to set a PIN now?"
And it keeps choking on my Razer DeathAdder drivers. Every 60 to 90 seconds I lose pointing ability, a second (or third, or fourth, or fifth) cursor shows up in whatever I'm doing, and I get the device disconnected/device reconnected bloop in my ears. It's a pointing device, Microsoft. It's the very basis of Windows. How can you be flubbing this so hard?!
They did:If there was a way to prevent it from requiring a PIN at install, they hid it deep.
https://support.microsoft.com/en-us...-create-a-local-user-or-administrator-account
The same steps apply during initial setup, they just don’t tell you that because of course they want you to sign up with a telemetry-gathering, usage-tracking Microsoft account.
Probably for the best. IIS isn’t exactly known for being very secure.I'm tired of trying to figure out how to get IIS to play nice... I'm just gonna download Fenix.
—Patrick
GasBandit
Staff member
It was for a purely internal website/wiki, so security wasn't a huge issue, but god damn did they want to obfuscate everything. I like it better when shit just works.Probably for the best. IIS isn’t exactly known for being very secure.
Heh. That is a phrase I do not normally associate with Microsoft. Some other company, maybe, but not Microsoft.I like it better when shit just works.
—Patrick
Last edited:
The part that I like most is that I already have a Microsoft account. I set it up when I worked there. It's secure as all hell and when it comes time to pick passwords, my general process is:They did:
https://support.microsoft.com/en-us...-create-a-local-user-or-administrator-account
The same steps apply during initial setup, they just don’t tell you that because of course they want you to sign up with a telemetry-gathering, usage-tracking Microsoft account.
Probably for the best. IIS isn’t exactly known for being very secure.
—Patrick
1. Go to Random.org/use dice and generate random numbers until you have 4 unique integers. These are going to be numeric and special characters for the password.
2. Also on Random.org, flip a coin four times. If the toss comes up heads, the integer stays a number, if it's tails, it becomes the special character version of that key.
3. Grab a dictionary. Pick two more random numbers (between 1 and how many pages your dictionary has). These two numbers are the page numbers for the alpha values in your password.
4. Go to those pages and pick two words that will combine into at least 10 characters. Salt the hell out of them with your random numbers/special characters and assorted capitalizations.
So please Microsoft, please tell me that pissing me off until I just set an angry curse as a password is more secure than, for instance, "3blUe&ro$lLeR8" where I generated 3, 5, 4, 8 - the 5 and 4 came up tails, and found blue and roller, then capitalized random letters. These words mean nothing to me. The numbers are completely insignificant to me in every way. They aren't a birthday, or a locker combo I had in elementary school, or part of a phone number. Blue isn't my favorite color, or my pet's name, or a street I lived on, and roller is just a six letter word that fills out the requirement for ten letters. You cannot social engineer this password out of me, it's unique to whichever site I generate it for, and then it gets written down until I can commit it to memory, and then burned. But no, I'm sure, 4 digits (and it wouldn't let me repeat numbers or use 1234, so they're self-limiting combinations to boot) or up to seven alphanumeric characters is sooooo much more secure. Hell, you want to take the human element out even more? Instead of using a dictionary and choosing words, go to a website with Captcha and use the two phrases that generate.
It would also be nice if Microsoft weren't running a massive botnet and using my computer as part of it.
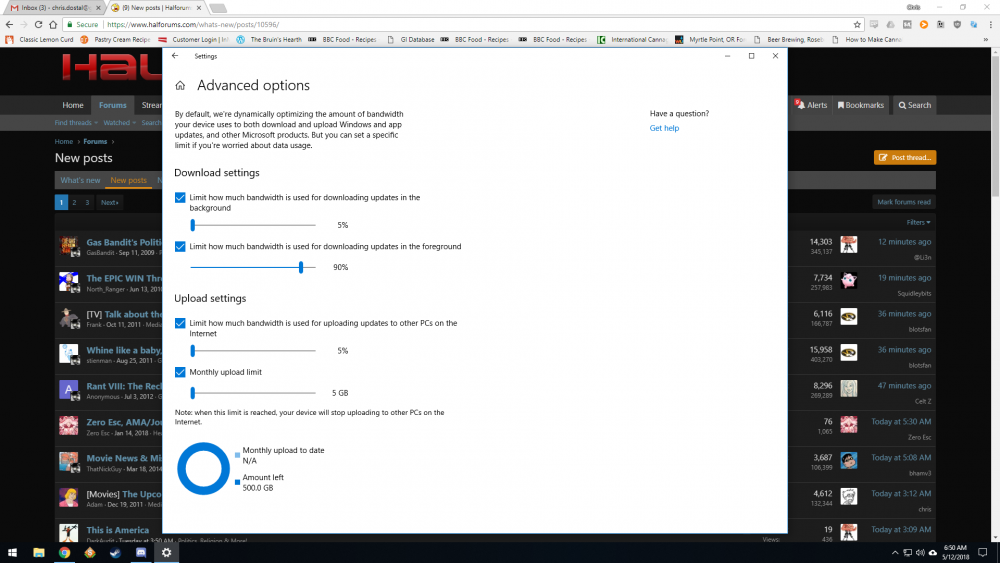
Yep... you can now set a bandwidth limit for how much Microsoft will use your PC to distribute Windows and Microsoft App store upgrades to other people's machines over the internet. You cannot, however, limit how much your PC downloads from other PCs on the internet, unrelated to you or yours. Sure hope every other person keeps their computer as secure as I keep mine.
Yep... you can now set a bandwidth limit for how much Microsoft will use your PC to distribute Windows and Microsoft App store upgrades to other people's machines over the internet. You cannot, however, limit how much your PC downloads from other PCs on the internet, unrelated to you or yours. Sure hope every other person keeps their computer as secure as I keep mine.
Previously this option only pertained to other computers connected to your network, allowing one download of an update to be distributed across all machines over Ethernet. They've now gone into randos over the internet?It would also be nice if Microsoft weren't running a massive botnet and using my computer as part of it.
View attachment 26808
Yep... you can now set a bandwidth limit for how much Microsoft will use your PC to distribute Windows and Microsoft App store upgrades to other people's machines over the internet. You cannot, however, limit how much your PC downloads from other PCs on the internet, unrelated to you or yours. Sure hope every other person keeps their computer as secure as I keep mine.
Microsoft thanks you for Doing Your Part(tm) and helping them keep distribution costs down.It would also be nice if Microsoft weren't running a massive botnet and using my computer as part of it.
Remember the mantra: “torrenting is illegal...except when we do it.”Previously this option only pertained to other computers connected to your network, allowing one download of an update to be distributed across all machines over Ethernet. They've now gone into randos over the internet?
—Patrick
Exactly, why should they pay for their CDN, when they can get the populace to use their bandwidth and eat up their bills (since you can't even force it to accept that you're on a metered connection any more, it just knows if you're lying). I'm actually, for the first time ever, considering unplugging my computer from the router every night.Microsoft thanks you for Doing Your Part(tm) and helping them keep distribution costs down.
Remember the mantra: “torrenting is illegal...except when we do it.”
—Patrick
Not if you're using an Intel 600-series SSD, it won't.And now it's time to play "Will It Update?" Starring Windows 10 version 1833!
--Patrick
Well, my mouse problem continues. And my keyboard problem only seems to act up while the mouse is acting up, so I did a little more digging through device manager and it looks like Windows is puking on everything that's connected to USB 3.0, and just keeps reinstalling HID compatible controllers over and over again trying to fix it. Anyone know how to troubleshoot a USB 3.0 compatibility issue in 1803?
I'm not entirely certain that there are any non-USB 3.0 ports on this board. There are a butt-load of USB ports on the back of my monitor, though.Start by finding out who made your USB3 controller?
Alternatively, disconnect everything from USB3, see if it keeps happening.
--Patrick
There should be, even if it means going through a header.I'm not entirely certain that there are any non-USB 3.0 ports on this board.
--Patrick
Huzzah! The 2.0 header is up by the lone remaining serial port, and the mouse and keyboard seem to be working flawlessly now! The external drive that's connected via USB 3 doesn't seem to be having any issues, thankfully, but every hour or so when the mouse and keyboard are connected, windows re-enables 8 separate HID compliant entries in the Device Manager and the mouse goes to shite. Tom's Hardware and others tell me that simply disabling the devices instead of uninstalling them will make it so Windows can't reinstall/re-enable them, but they are wrong.There should be, even if it means going through a header.
--Patrick
